Outlook OAuth2 provider¶
Prerequisites¶
git checkout origin/osp-communications .
Warning
To add a new application and get all necessary information for the configuration of the Oauth via azure you have to be admin or be validated by the admin of your system.
Glossary¶
Tenant : The tenant is the Directory (tenant) ID. You have to pass it to declare the Authority. ClientID : The clientId is the Application (client) ID. You have to pass it so that it is possible to check the client rights (application).
Known error of configuration¶
Warning
If you get an 535-5-7-139 error you can check this tutorial (https://ourcloudnetwork.com/how-to-fix-error-535-5-7-139-authentication-unsuccessful/). The most common reason you are receiving this error is that the application or device trying to send the email is using SMTP basic authentication. As of 1st October 2022, Microsoft automatically disabled SMTP based authentication in Exchange Online.
Description¶
Note
An example for a notification configuration is available <a href=”../010_configure-aspsms-notification”>here</a>.
In this tutorial you will learn to :
Configure Azure/Outlook to let the module send email through its services
Configure the provider
Configuration structure¶
![@startuml
skinparam backgroundColor transparent
package "modules" as modules {
node ospcoms as "osp-communications"
}
package "root" as root {
package "providerOAuth2" as provider {
[providers.coms] as provComs
[value.ospp] as valueSMS
}
[dashboard.view] as dash
}
ospcoms -[#black]-> provComs : **Own**
valueSMS -[#black]-> dash : **Give provider status**
@enduml](../../_images/plantuml-5e2cf4cceec8cdff0ce8c8ee7b26b51aef092664.png)
Steps¶
Note
Note that Microsoft may change the way things work. This tutorial has been tested the 11 May 2023.
1. Go to your Azure account and configure a new application¶
Go to your azure portal.
Go to App registrations.
Click on New Registration
Give the application the name you want (for exemple OnSphereCommunications) and check Accounts in any organizational directory (Any Azure AD directory - Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox). Confirm using the Register button.
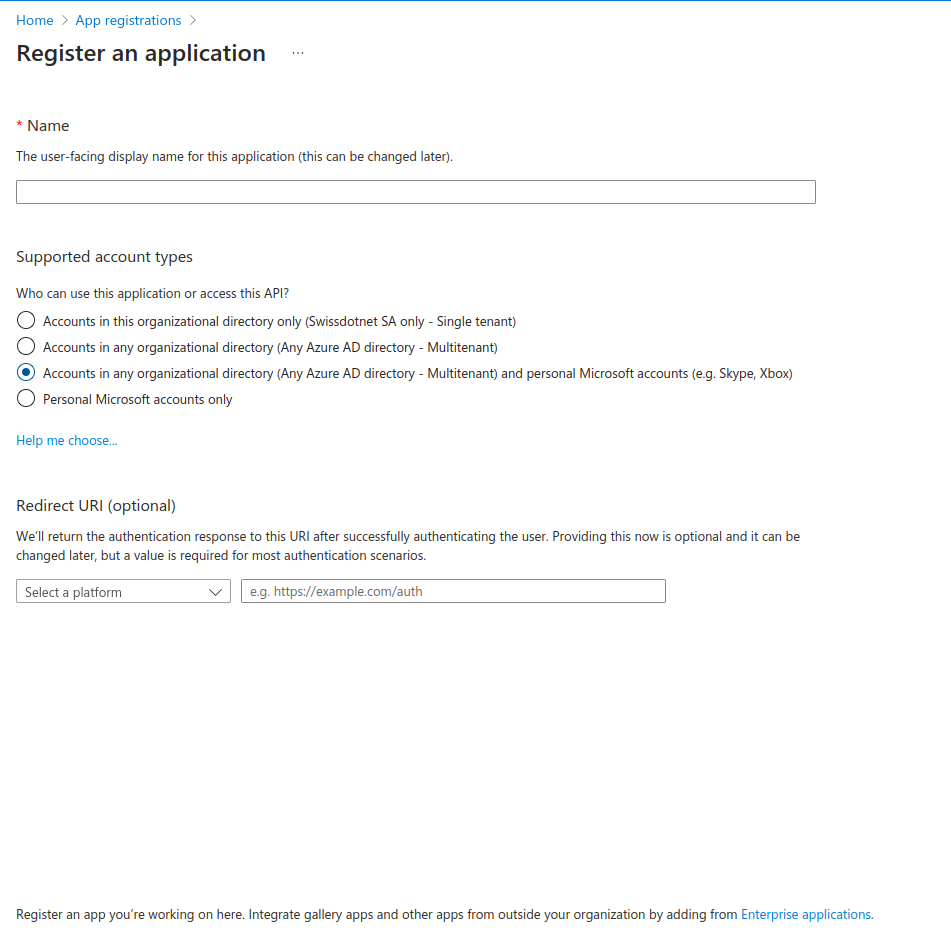
Save the application Application (client) ID.
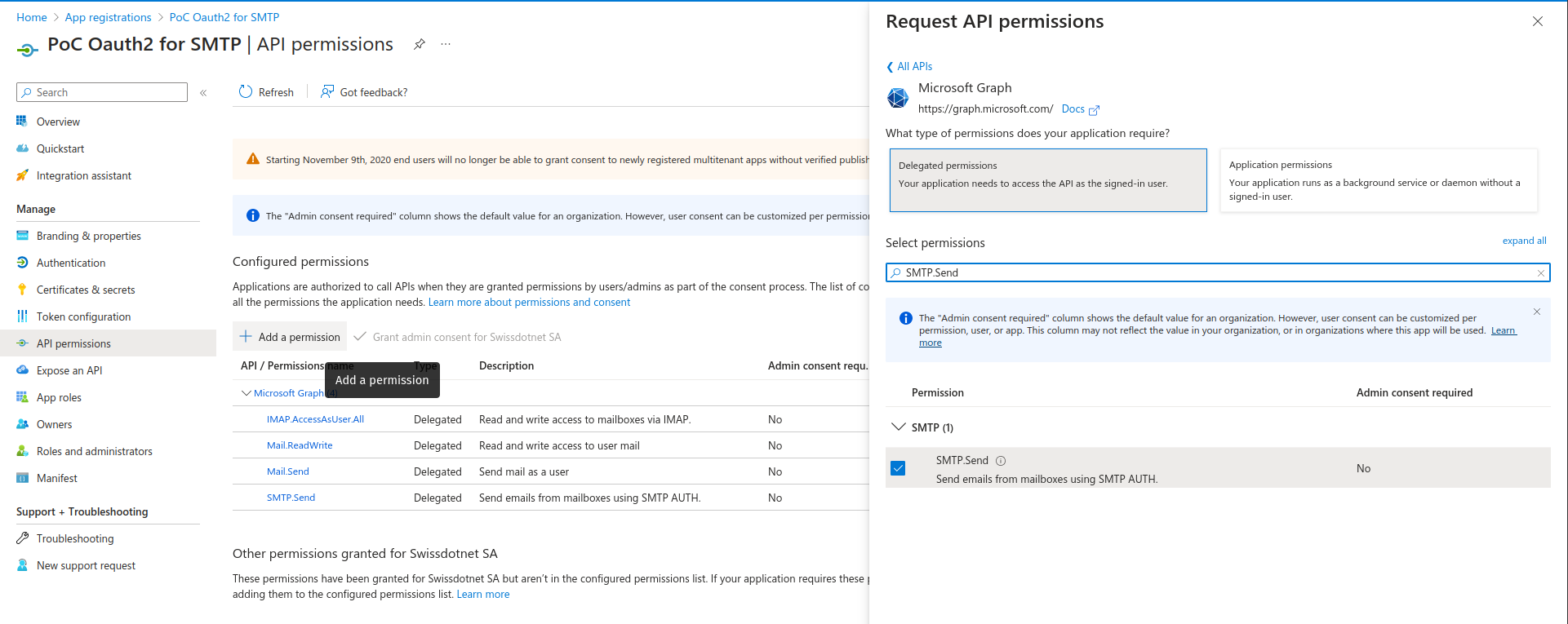
Go the the API permissions tab of your application
Click on + Add a permission
Click on Microsoft Graph
Click on Delegated permissions
Here you will have to add the following settings by checking the box (you can copy paste the text bellow inside the Select permissions text input bar) :
Mail.ReadWrite
Mail.Send
SMTP.Send
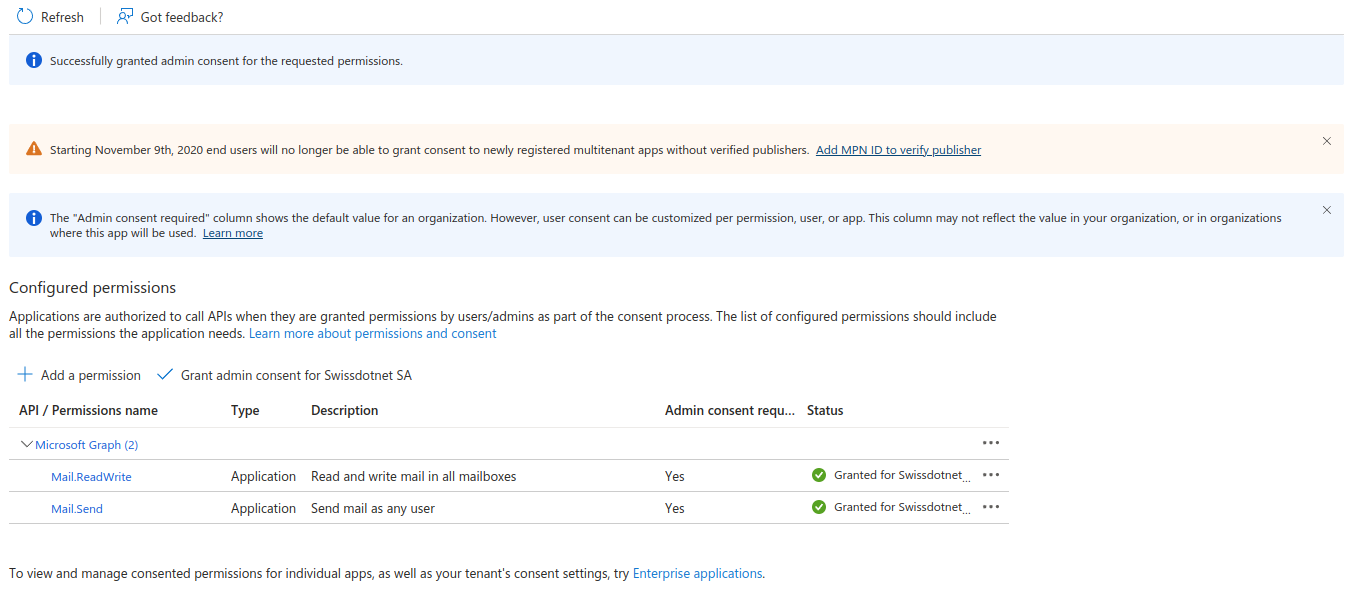
Verify that it is validated by an admin (under the Status column there should be a green check mark)
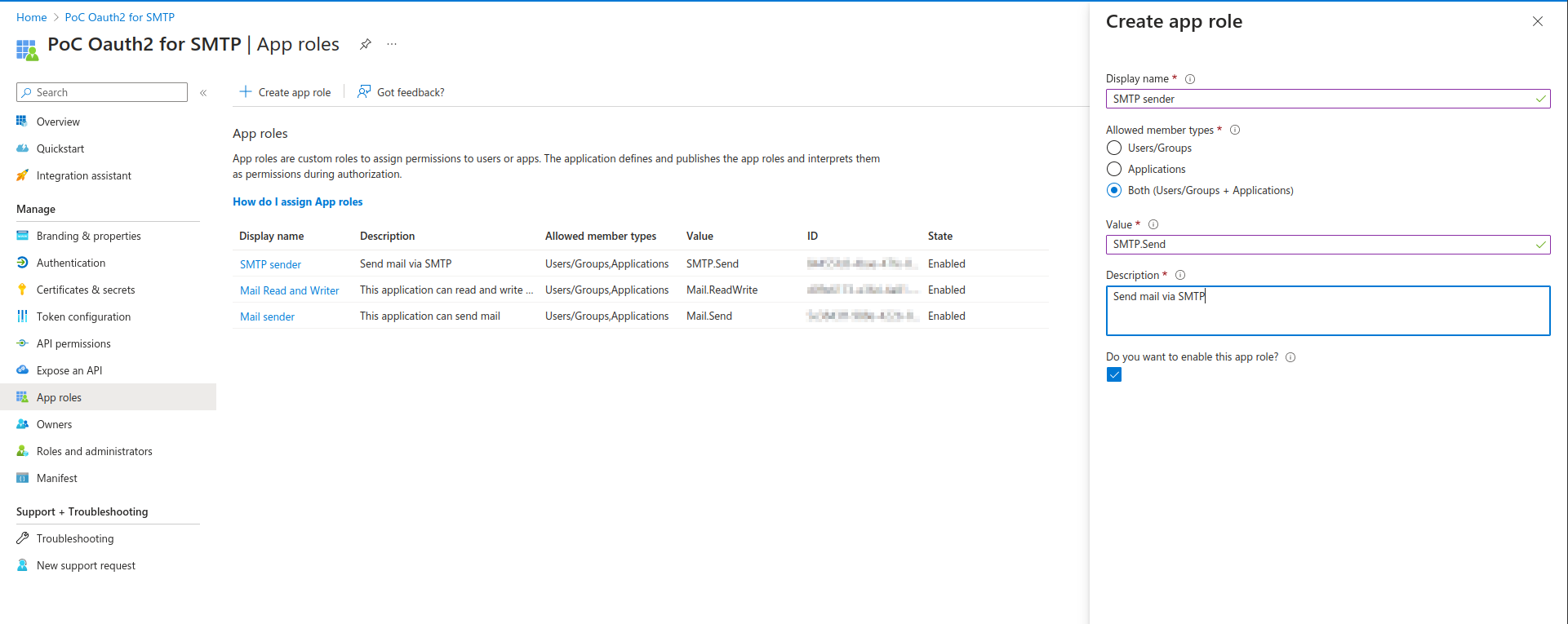
Once this is done you can click on App roles (side menu).
Click on + Create app role. You will have to do this 3 times.
Create an app role for SMTP.Send
Create an app role for Mail.Send
Create an app role for Mail.ReadWrite
Don’t forget to fill the fields :
Display Name. Fill with a name that makes sense for you
Check Both in allowed member types
Value. this should be (SMTP.Send, Mail.Send and Mail.ReadWrite)
Description. Fill with a description that makes sense for you
Once every thing is configured you can go to the next step.
Warning
If you encounter any configuration problem please contact your Azure AD administrator.
2. Configure the provider using OAuth2¶
root/providerGmail/provider.coms
{
"moduleId": "modules.communications.communications-1",
"providerType": "EMAIL",
"authenticationConfiguration": {
"type": "OUTLOOK_OAUTH2",
"username": "${YOUR_EMAIL}",
"authority": "https://login.microsoftonline.com/${YOUR_TENANT_ID}",
"clientId": "${YOUR_CLIENT_ID}",
"passwordProvider": {
"password": "${YOUR_PASSWORD}",
"type": "PLAINTEXT"
},
"scope": [
"https://outlook.office365.com/.default"
]
},
"sendingProtocol": {
"type": "SMTP",
"smtpHostServer": "smtp.office365.com",
"port": 587
}
}
root/providerGmail/value.ospp
{
"name": "OAuth2 Provider Value",
"description": "",
"type": "BOOLEAN"
}