Single sign-on or SSO
The SSO allows OnSphere to delegate the authentication and user management to an external system. The user will be able to navigate between multiple system without having to re-authenticate every time.
We support two protocol for the SSO.
Both provide an IDP which as its name implies provide an identity and manage it.
For both protocols, OnSphere needs some default information to improve the user experience. See the Mapper for the configuration.
Email
Username
Last name
First name
If some required information are missing, we will prompt the user to fill them.
Note
This guide does not describe how to configure your IDP to use either protocol. Please refer to your IDP documentation.
Configuration
The configuration for both protocol is done on the Identity providers tab of the Keycloak management interface.
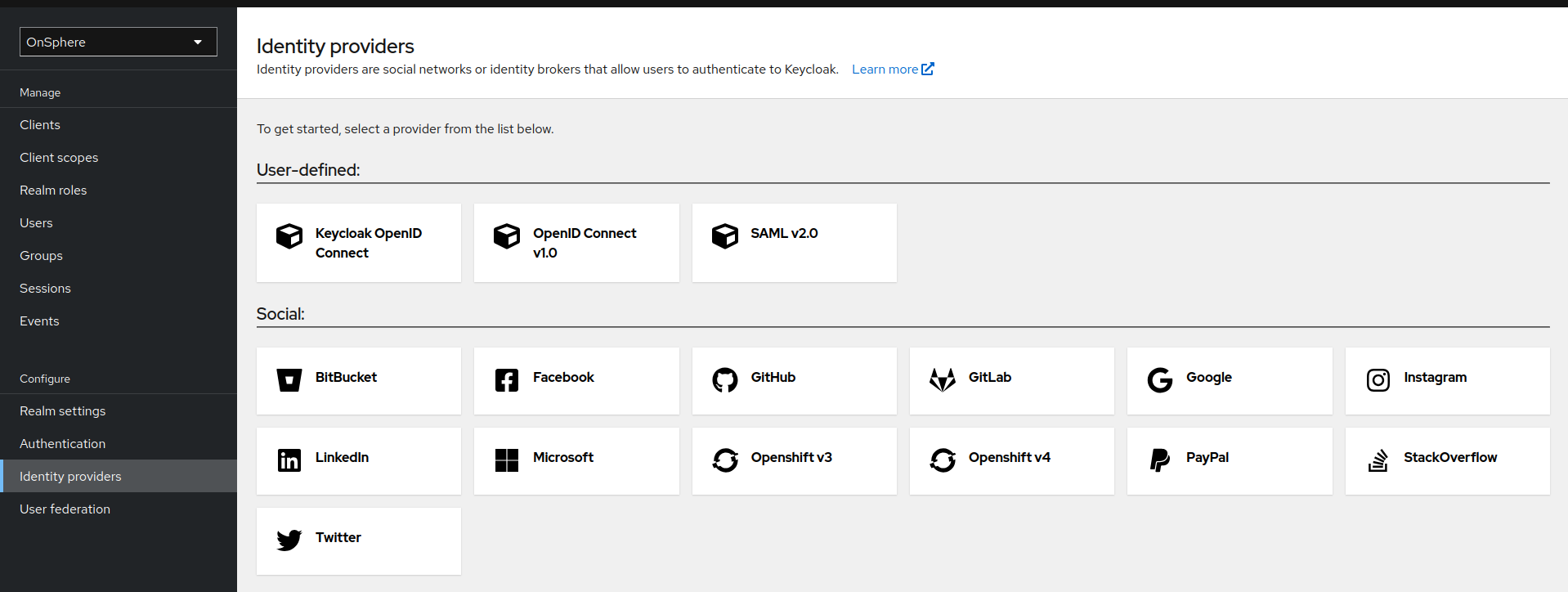
OpenID Connect or OIDC
To configure an OIDC IDP, you will need the following information before starting.
The discovery endpoint from your IDP, formatted like this https://<idp hostname>/<specific path>/.well-known/openid-configuration.
A client ID.
A client secret.
The redirect URL required by the IDP will be provided by Keycloak during the configuration of the provider.
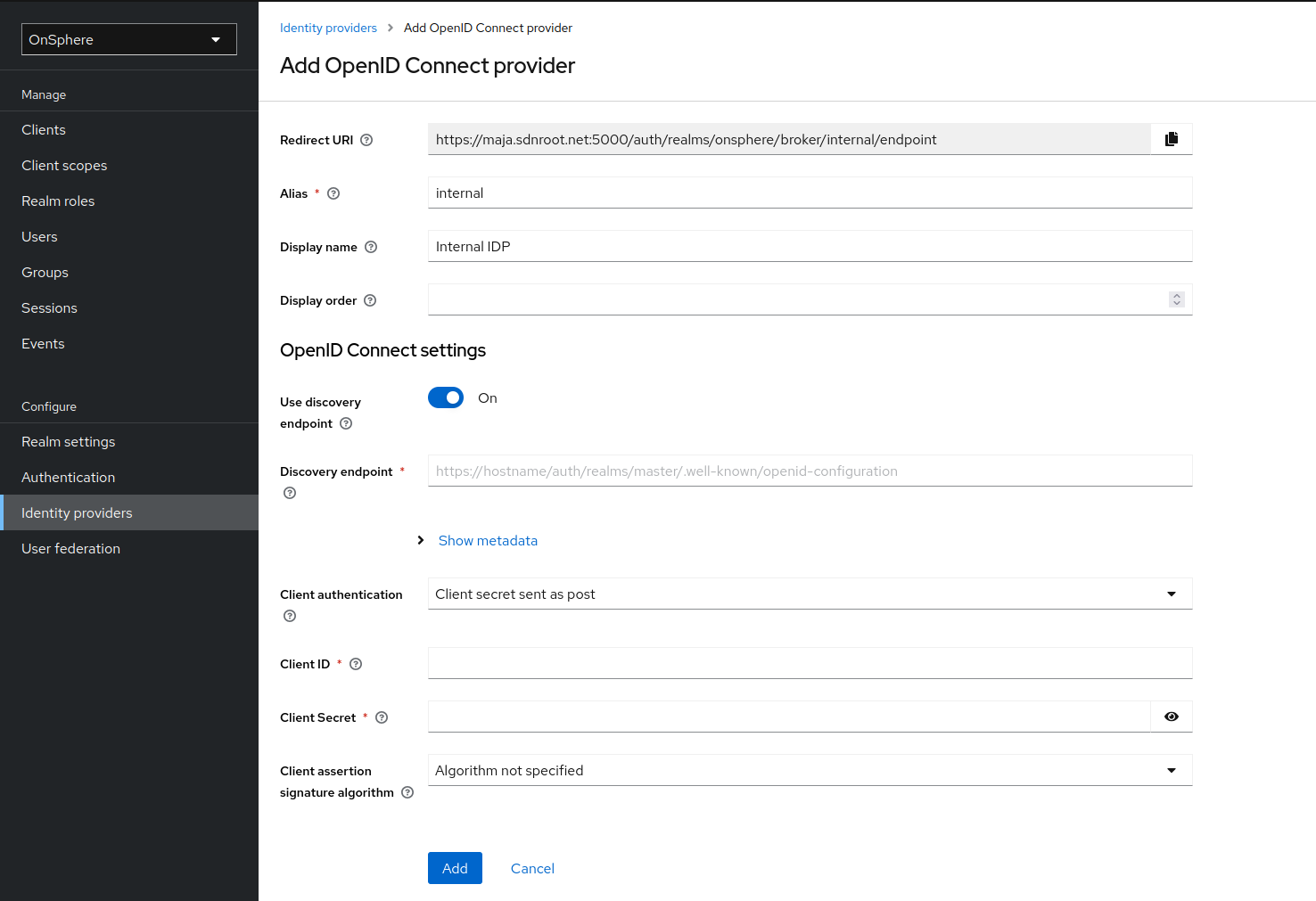
When all required information are provided, you can Add the provider.
Depending on the configuration of your IDP, it may be necessary to add some scopes to the OIDC configuration.
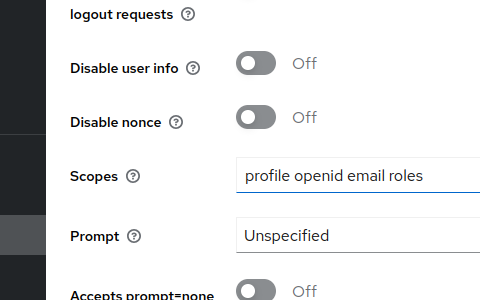
The common ones are
openid: This is mandatory. It is added automatically if no others are defined.
profile: This allows Keycloak to access profile information about the current user.
Email: This allows Keycloak to access email information about the current user.
You can already test if the communication is valid by going to the OnSphere login page.
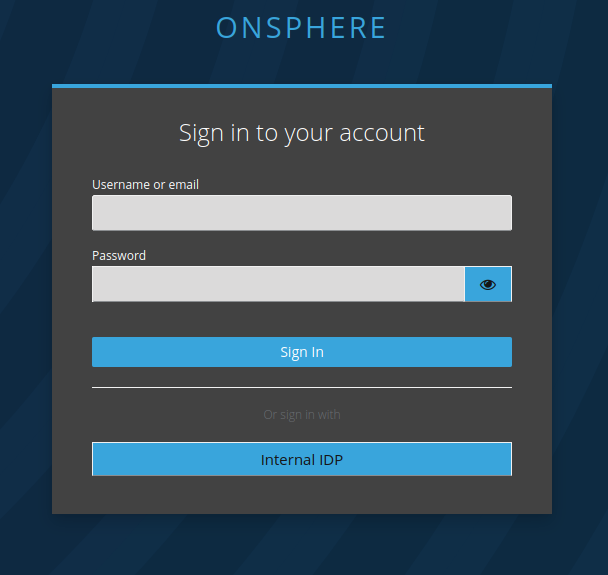
You can login by using the Internal IDP button. You should be redirected to your IDP login page and when you enter your credentials redirected to OnSphere.
SAML 2.0
To configure a SAML IDP, you will need the following information before starting.
The entity descriptor from your IDP, formatted like this https://<idp hostname>/<specific path>/FederationMetadata/2007-06/FederationMetadata.xml.
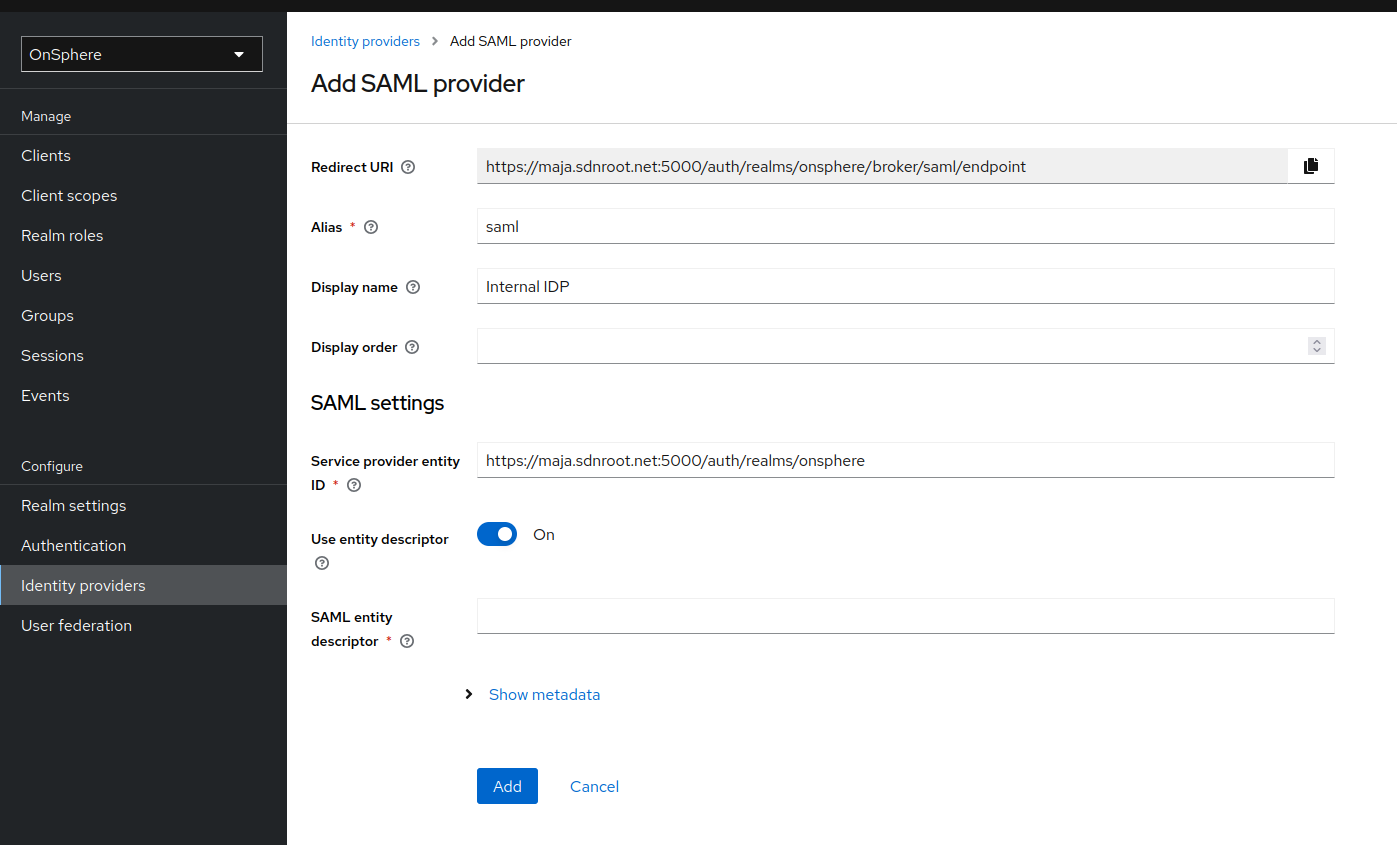
When all required information are provided, you can Add the provider.
The endpoint descriptor URL required by the IDP will be provided by Keycloak during the provider configuration.
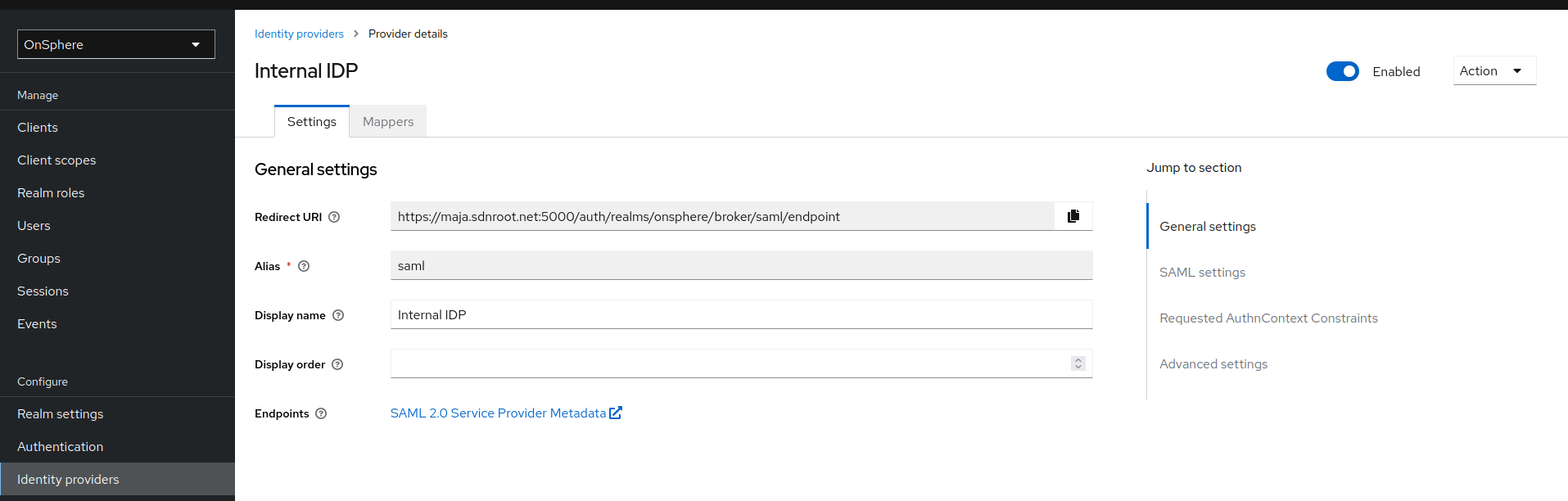
This is needed to configure the IDP to accept the communication.
You can already test if the communication is valid by going to the OnSphere login page.

You can login by using the Internal IDP button. You should be redirected to your IDP login page and when you enter your credentials redirected to OnSphere.
Synchronization
Another important configuration to consider is the Sync Mode. This determines when user information is synchronized between Keycloak and the IDP. This is useful if a user group, email or other information changes.
Import: Synchronize user information only at first login. This means that changes made to the IDP will not be propagated.
Force: Synchronize user information on every connection. This means that changes made to the IDP will be propagated.

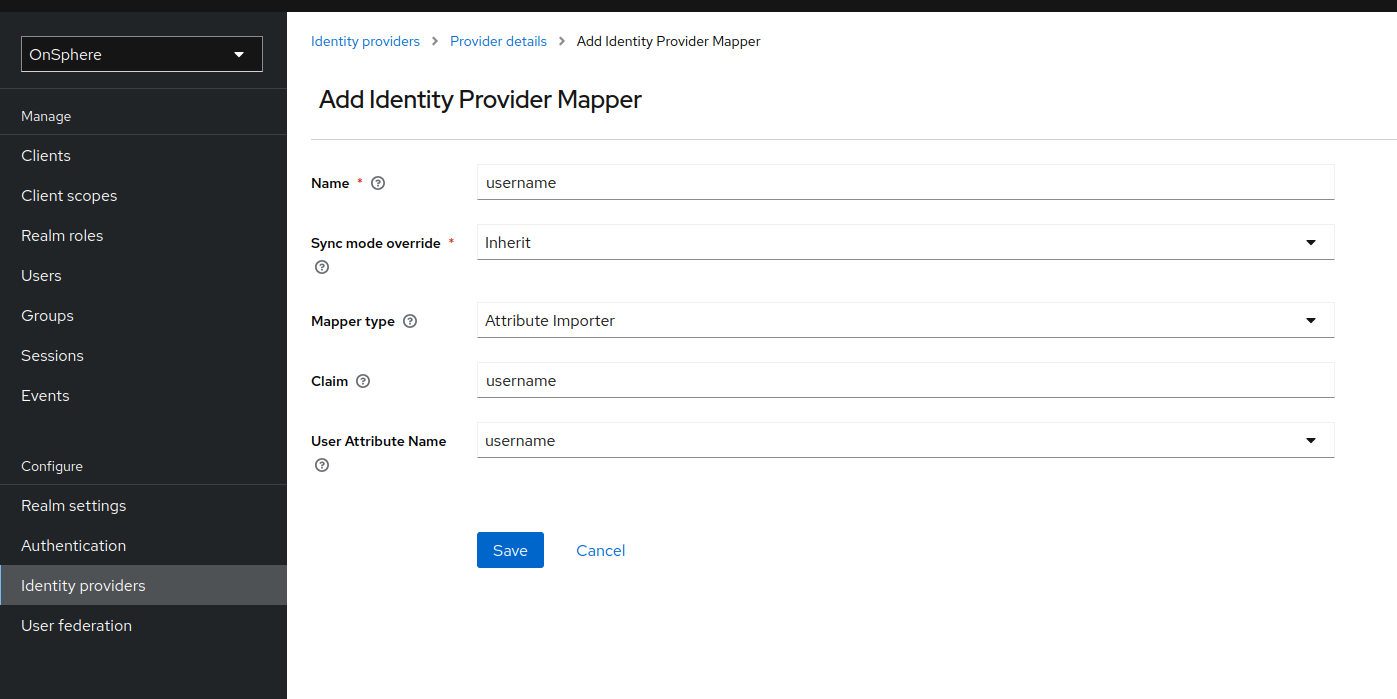
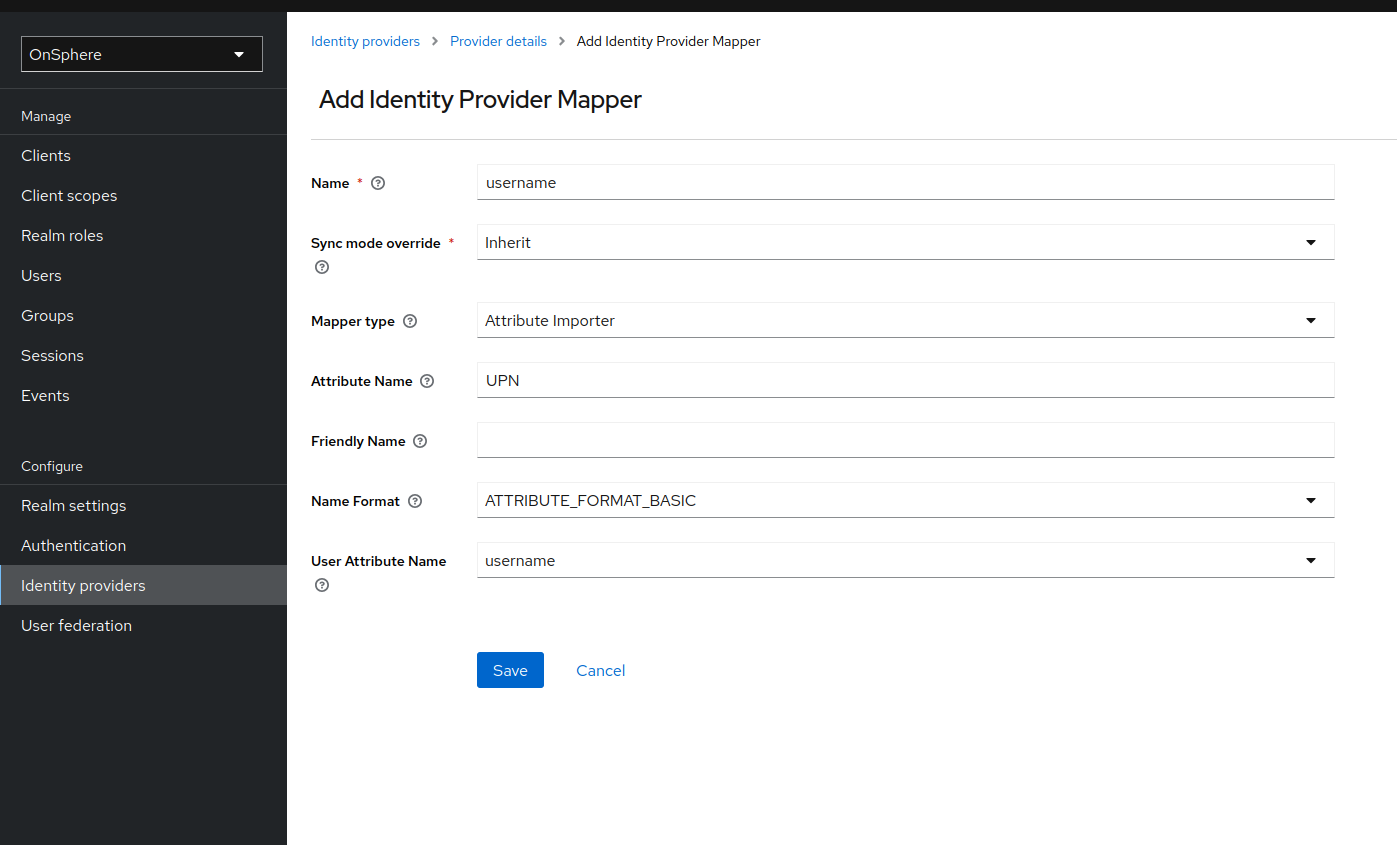
Mapper
To fill the user information, you need a mapper for each attribute.
Below an example for the username mapper for SAML and OIDC.
SAML
The field Attribute Name, Friendly Name and Name Format will be dependent of the IDP configuration.
OIDC
The field Claim will be dependent of the IDP configuration.