Users security
Users security means authenticating user as well as restricting their access to resources.
Authentication is done by Keycloak while users resources access is managed by osp-rights
A default deployed OnSphere stack have the following user automatically created :
User |
Default password |
Configuration clone |
Keycloak user management |
Dashboard access |
|---|---|---|---|---|
administrator |
onsphere |
yes |
yes |
no |
supervisor |
onsphere |
no |
yes |
yes |
user |
onsphere |
no |
no |
yes |
Authenticating
Authentication is done by Keycloak, usually when users try to log-in through the Login page, but other means are also available.
Webhooks apiKey
When using webhooks authentication is done using an API Key. Process to authenticate on webhook using API Key is described in Webhooks documentation.
URL authentication
An authentication based on credentials passed inside the URL can be configured and enabled for a user or group. This enable a user to connect into OnSphere without having to go through a login form.
The url becomes : <stack-ip>:<front-end-port>/home/root?authentication=SGVsbG8gdGhlcmUgIQ==
Note
Uses “The Base64 Alphabet” as specified in Table 1 of RFC 4648 and RFC 2045 for encoding and decoding operation
You need to add the credentials in base64 following the format user:password. You add this information as a authentication parameter. If given credentials are correct and the user has the rights to use this authentication method, you will be directly redirected to the dashboard specified in the URL. Otherwise, there can be different outcomes :
If the user doesn’t have the rights, you are redirected to the login form
If the user has the rights but the credentials are invalid, you are redirected to the login form.
Keycloak configuration
Roles
You need to have a realm role defined as url_auth. The users or groups that want this authentication need to have that role assigned to them.
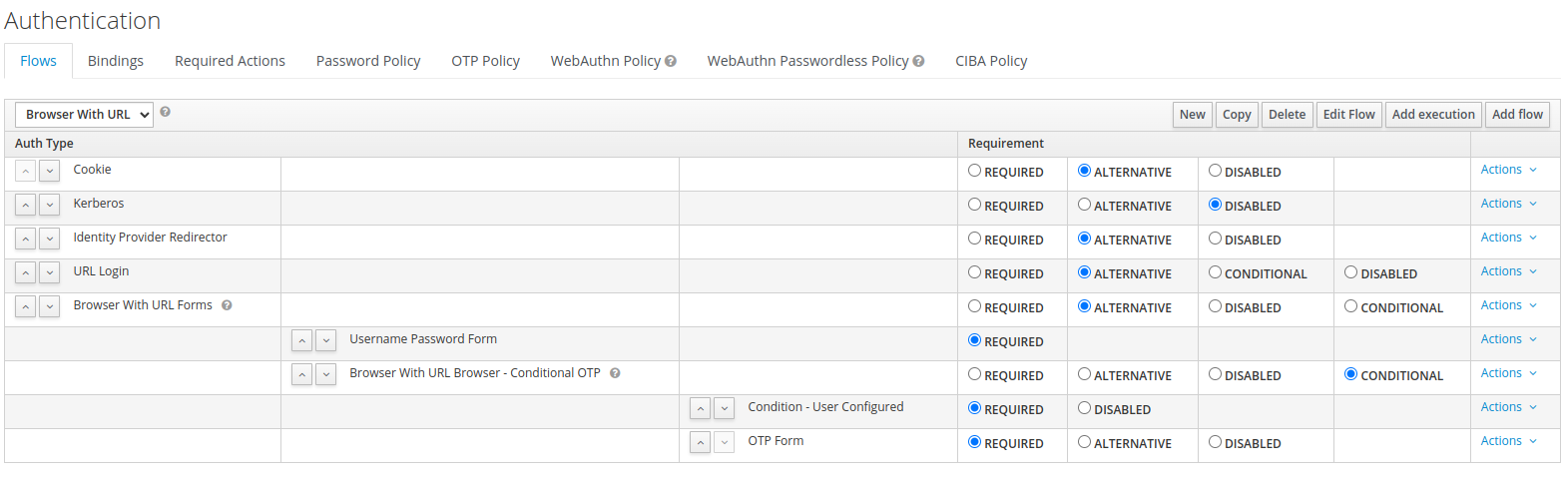
Adding authentication flow
You need to add a step into the browser authentication flow, but you can’t modify the default one. To do so :
Select the Browser flow and make a copy
Add an execution with the provider URL Login
Move the URL Login step before the Forms
Enable the URL Login step by making it Alternative
In the bindings tab, replace the browser flow with the one just created
Your authentication flow should look like :
Resources access rights management
Resources can be divided in two :
High level system (administration) resources
Low level data (business) resources
By default, five groups are defined, four for high level system resources :
configuration-management: Give access to the configuration withgit clone.user-management: Give access to the users management page.administrator: This group has all the right of the group above.user: Give the access to the account and profile management panel for the user.
and one for low level data resources :
data-access: Give access to the data. (By default grant access for all values. See Feature rights for more information.)
Access to values, dashboards, scripts, actions, … can be controlled with this feature.
Principle
The rights are managed as a tree base on the directory. This implies that an element in a sub-directory will (by default) inherit the right of its parent.
The following access level exist :
READ: Allow to read the element.WRITE: Allow modification of the element (Publish a value, run a script, execute a request).
These rights are based on the group membership of the user as define on Keycloak.
The file access.rights allow to modify the rights for a sub-tree.
Warning
access.rights is mandatory on the root folder.
There are three keywords used to define the rights :
override: Reset the right with the one define here.include: Add a new group from the access level.exclude: Remove a group from the access level.
Note
override is exclusive with include and exclude.